- Built for CI/CD and DevOps: Seeker is easy to deploy and scale in your CI/CD development workflows. Native integrations, web APIs, and plugins provide seamless integration with the tools you use for on-premises, cloud-based, microservices-based, and container-based development. You’ll get accurate results out of the box, without extensive configuration, custom services, or tuning. Seeker monitors web app interactions in the background during normal testing and can quickly process hundreds of thousands of HTTP(S) requests, giving you results in seconds with near-zero false positives—no need to run manual security scans.
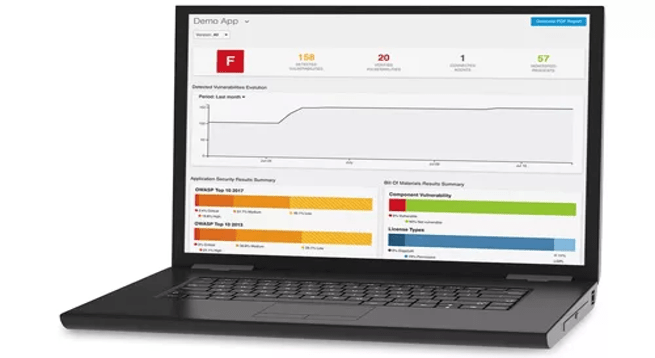
- Streamlines security compliance and remediation: Seeker makes security compliance reporting easy. Detailed dashboards show compliance with OWASP Top 10, PCI DSS, GDPR, and CWE/SANS Top 25, as well as alerts when applications expose sensitive information (valuable to help ensure compliance with PCI DSS and GDPR). Seeker also pinpoints vulnerable lines of code and provides detailed contextual remediation advice e-learning which helps your development teams learn and fix vulnerabilities quickly.
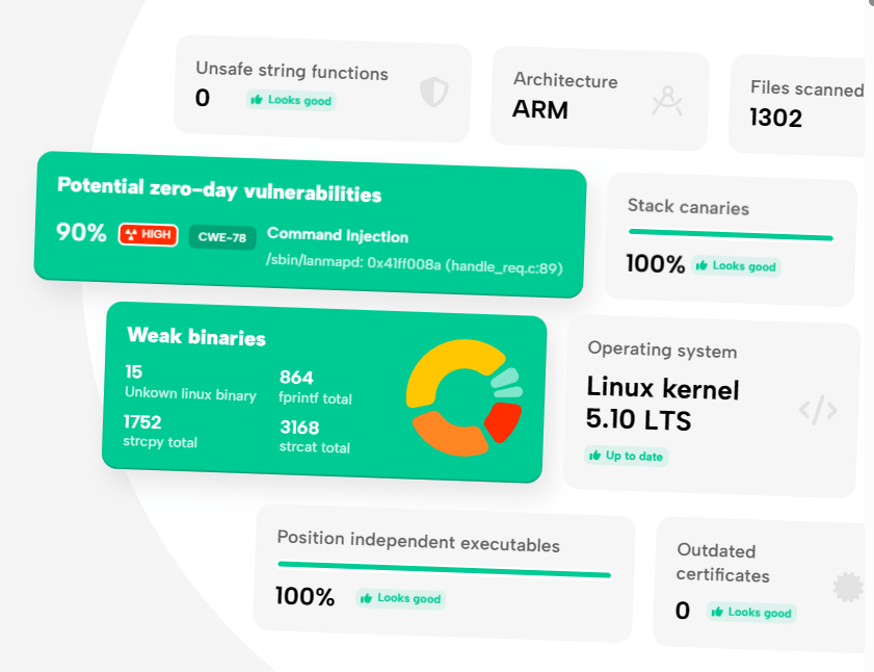
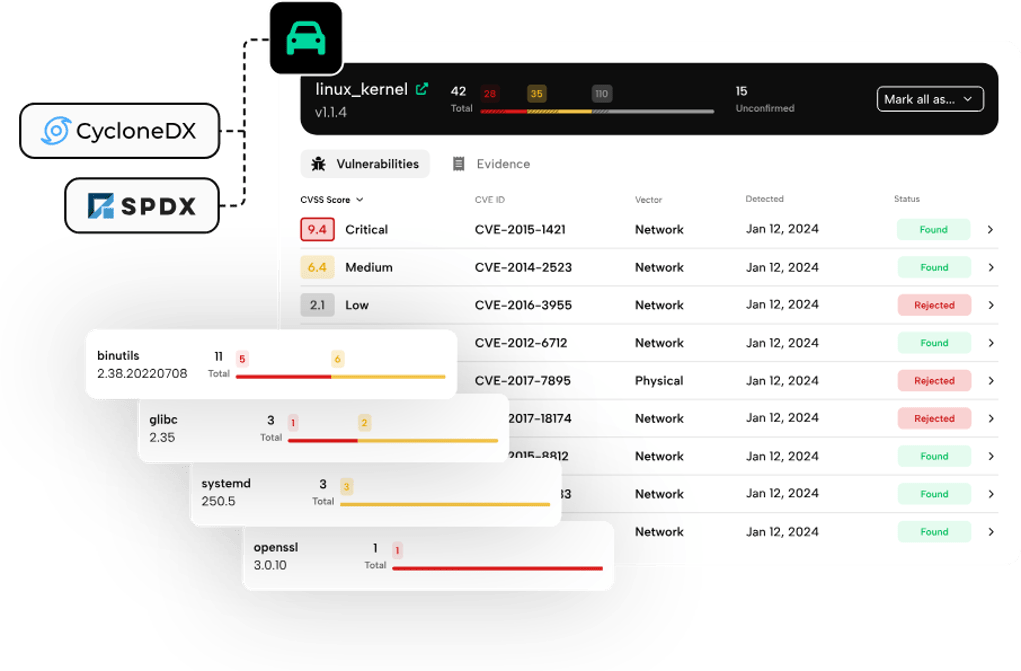
- Identifies risk in open source and third-party libraries: Seeker integrates Black Duck Binary Analysis, which analyzes target binaries for open source security vulnerabilities, versioning, and license type information. You’ll get a unified view of all identified vulnerabilities found in custom code and component libraries.
Seeker Interactive Application Security Testing
Seeker is an interactive application security testing (or IAST) solution that can scale to thousands of apps. Unlike dynamic analysis (or DAST) solutions, Seeker complements static analysis, detecting vulnerabilities using instrumentation to analyze code, dataflow, and memory in the background while the app is under test. Seeker IAST enables dev teams to find and confirm exploitable vulnerabilities across multitiered web apps and integrate runtime code analysis.



Reviews
There are no reviews yet.